Nist To Cis Mapping – Cross-Mapping the NIST Framework with Data Security Standards These standards are: Center for Internet Security (CIS) Controls: These universally recognized controls provide actionable . As NIST’s guidance notes, differential privacy can be leveraged as a scheme to evaluate an organization’s digital privacy posture through a framework that identifies existing factors to .
Nist To Cis Mapping
Source : www.cisecurity.org
Mapping and Compliance
Source : www.cisecurity.org
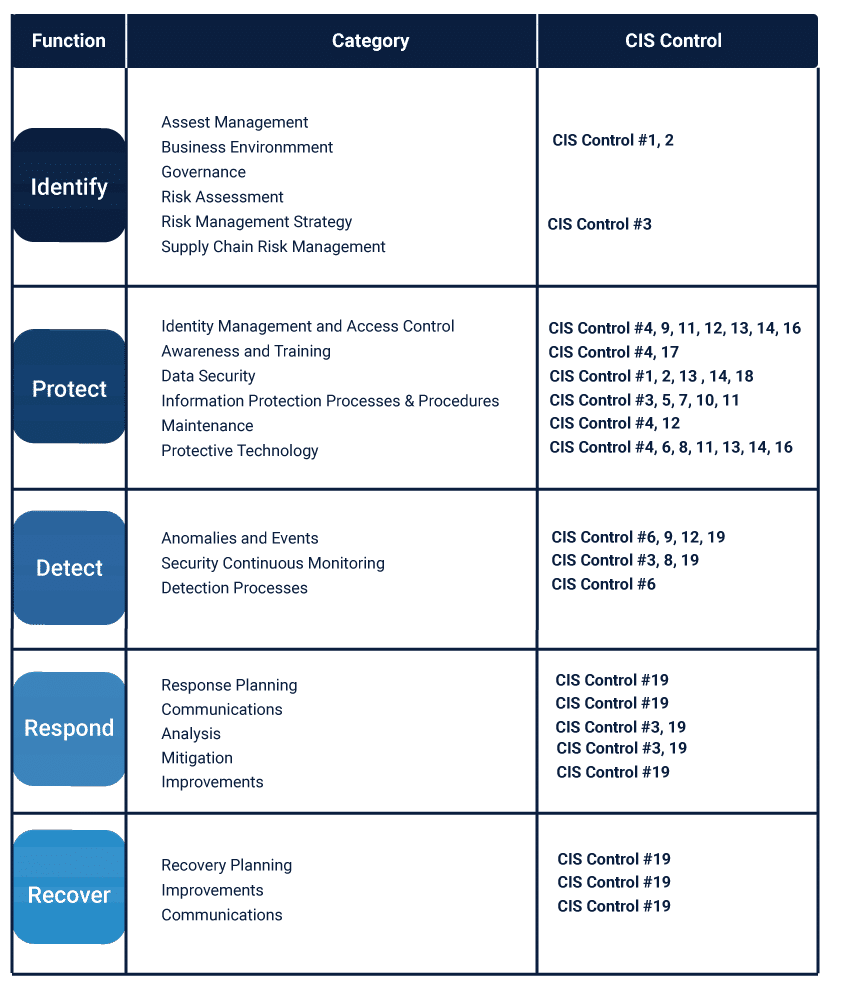
CIS Critical Security Controls v8 Mapping to NIST CSF
Source : www.cisecurity.org
How to make sense of Cybersecurity Frameworks Cuelogic An LTI
Source : www.cuelogic.com
CIS Critical Security Controls v8 Mapping to NIST CSF
Source : www.cisecurity.org
CIS vs. NIST: A Comprehensive Comparison | Tentacle Blog
Source : tentacle.co
CISControls v7.1 Mapping to NIST CSF
Source : www.cisecurity.org
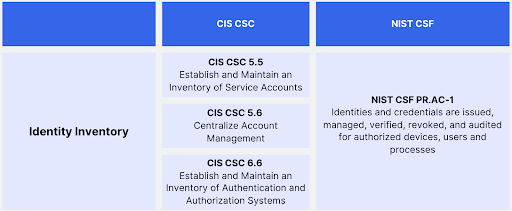
Strengthening Identity Controls: Mapping to CIS CSC and NIST CSF
Source : oort.io
CIS Critical Security Controls v8 Mapping to NIST 800 53 Rev. 5
Source : www.cisecurity.org
Rethink Cyber: (NCSF+CSC)xCKC™ = BFD
Source : www.linkedin.com
Nist To Cis Mapping CISControls v7.1 Mapping to NIST CSF: After receiving the final rose in the “Golden Bachelor,” Ms. Nist, 70, spoke about getting to know her new fiancé. First order of business: teaching him how to pronounce her name. By Callie . The first season of “The Golden Bachelor” has finished airing, and that means Gerry Turner and Theresa Nist can be public about their engagement. It did not take long for Nist to start sharing .